Step 1: Add a Domain Name to WAF (Cloud - CNAME Access)
This topic describes how to add a domain name to WAF in CNAME access mode so that the website traffic can pass through WAF. After you connect a website domain name to your WAF instance, WAF works as a reverse proxy between the client and the server. The real IP address of the server is hidden and only the IP address of WAF is visible to web visitors.

If you have enabled enterprise projects, you can select your enterprise project from the Enterprise Project drop-down list and add domain names of websites to be protected in the project.
Prerequisites
You have purchased a cloud WAF instance.
Constraints
Specification Limitations
After your website is connected to WAF, you can upload a file no larger than 10 GB each time.
Impact on the System
If a non-standard port is configured, the visitors need to add the non-standard port to the end of the website address when they access the website. Otherwise, a 404 error will occur. If a 404 error occurs, see How Do I Troubleshoot 404/502/504 Errors?
Procedure
- Log in to the management console.
- Click
 in the upper left corner of the management console and select a region or project.
in the upper left corner of the management console and select a region or project. - Click
 in the upper left corner and choose Web Application Firewall under Security & Compliance.
in the upper left corner and choose Web Application Firewall under Security & Compliance. - In the navigation pane, choose Website Settings.
- In the upper left corner of the website list, click Add Website.
- Select Cloud - CNAME and click OK.
- Provide the domain name details.
- Website Name: (Optional) You can customize the website name.
- Domain Name: Enter the domain name you want WAF to protect. You can enter a top-level single domain name, like example.com, a second-level domain name, like www.example.com, or a wildcard domain name, like *.example.com.
If your domain name is hosted on Huawei Cloud, you can click Quick Add Domain Names Hosted on Cloud. In the Select Domain Name dialog box displayed, select the domain name you want to protect and click OK. The hosted domain name is automatically added to WAF.

- The following are the rules for adding wildcards to domain names:
- If wildcard (*) is added to WAF, only non-standard ports other than 80 and 443 can be protected.
- If the server IP address of each subdomain name is the same, enter a wildcard domain name to be protected. For example, if the subdomain names a.example.com, b.example.com, and c.example.com have the same server IP address, you can add the wildcard domain name *.example.com to WAF to protect all three.
- If the server IP addresses of subdomain names are different, add subdomain names as single domain names one by one.
- The following are the rules for adding wildcards to domain names:
- Website Remarks: (Optional) You can provide remarks about your website if you want.
Figure 1 Configuring domain name details
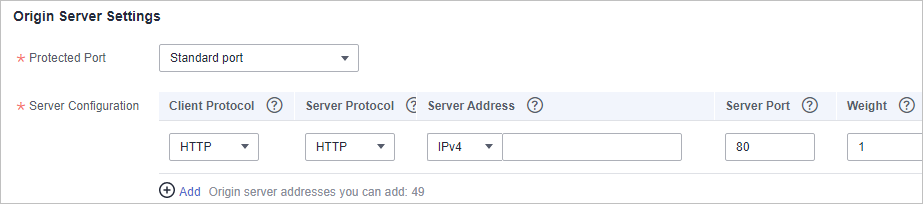
- Configure the origin server. Table 1 describes the parameters. Figure 2 shows an example.
Table 1 Parameter description Parameter
Description
Example Value
Protected Port
Select the port type that you want WAF to protect from the drop-down list.
To protect port 80 or 443, select Standard port from the drop-down list.
For details about ports supported by WAF, see Ports Supported by WAF.
NOTE:If a port other than 80 or 443 is configured, the visitors need to add the non-standard port to the end of the website address when they access the website. Otherwise, a 404 error will occur. If a 404 error occurs, see How Do I Troubleshoot 404/502/504 Errors?
81
Server Configuration
Configurations of your web server address. You need to configure the client protocol, server protocol, server weights, server address, and server port.
- Client Protocol: protocol used by a client to access a server. The options are HTTP and HTTPS.
If you set Client Protocol to HTTPS, HTTP/2 can be enabled. For details, see Enabling HTTP/2.
- Server Protocol: protocol used by WAF to forward client requests. The options are HTTP and HTTPS.
NOTE:
- For details about configuring Client Protocol and Server Protocol, see Example 4: Configuring Protocols for Different Access Methods.
- WAF can check WebSocket and WebSockets request, which is enabled by default.
- Server Address: public IP address (generally corresponding to the A record of the domain name configured on the DNS) or domain name (generally corresponding to the CNAME of the domain name configured on the DNS) of the web server that a client accesses. The following IP address formats are supported:
- IPv4 address, for example, XX.XXX.1.1
- IPv6 address, for example, fe80:0000:0000:0000:0000:0000:0000:0000
NOTICE:Only the professional and platinum editions support IPv6 protection.
- Server Port: service port over which the WAF instance forwards client requests to the origin server.
- Weight: Requests are distributed across backend origin servers based on the load balancing algorithm you select and the weight you assign to each server.
Client Protocol: HTTP
Server Protocol: HTTP
Server Address: XXX.XXX.1.1
Server Port: 80
Certificate Name
If you set Client Protocol to HTTPS, an SSL certificate is required. You can select a created certificate or import a certificate. For details about how to import a certificate, see Importing a New Certificate.
The imported certificates are listed on the Certificates page. For more details, see Uploading a Certificate.
Alternatively, you can buy a certificate on the CCM console and push it to WAF. For details about how to push an SSL certificate in CCM to WAF, see Pushing an SSL Certificate to Other Cloud Services.
NOTICE:- Only .pem certificates can be used in WAF. If the certificate is not in .pem format, convert it into .pem by referring to Table 3 before uploading the certificate.
- Currently, certificates purchased in Huawei Cloud SCM can be pushed only to the default enterprise project. For other enterprise projects, SSL certificates pushed by SCM cannot be used.
- If your website certificate is about to expire, purchase a new certificate before the expiration date and update the certificate associated with the website in WAF.
WAF can send notifications if a certificate expires. You can configure such notifications on the Notifications page. For details, see Enabling Alarm Notifications.
- Each domain name must have a certificate associated. A wildcard domain name can only use a wildcard domain certificate. If you only have single-domain certificates, add domain names one by one in WAF.
--
- Client Protocol: protocol used by a client to access a server. The options are HTTP and HTTPS.
- Complete advanced settings.
Figure 3 Advanced Settings
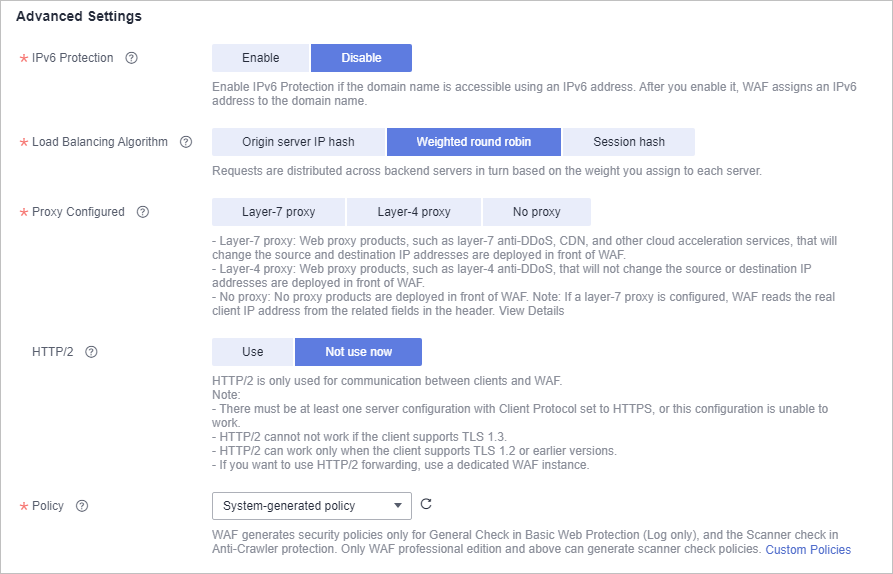
- IPv6 Protection: Enable IPv6 Protection if the domain name is accessible using an IPv6 address. After you enable it, WAF assigns an IPv6 address to the domain name.
- If you select IPv6 for Server Address, IPv6 Protection is enabled by default.
- If you select IPv4 for Server Address and enable IPv6 Protection, WAF will assign an IPv6 address to the domain name so that the website is accessible over the IPv6 address. In this way, requests to the IPv6 address are routed by WAF to the IPv4 address of the origin server.

If the origin server uses IPv6 addresses, IPv6 protection is enabled by default. To prevent IPv6 service from interruption, keep the IPv6 protection enabled. If IPv6 protection is not needed, edit the server configuration and delete IPv6 configuration from the origin server first. For details, see Editing Server Information.
- Load Balancing Algorithm: Select an algorithm.
- Origin server IP hash: Requests from the same IP address are routed to the same backend server.
- Weighted round robin: All requests are distributed across origin servers in turn based on weights set to each origin server. The origin server with a larger weight receives more requests than others.
- Session hash: Requests with the same session tag are routed to the same origin server. To enable this algorithm, configure traffic identifiers for known attack sources, or Session hash algorithm cannot take effect.
For details, see Switching the Load Balancing Algorithm.
- Configure Proxy Configured.
- Layer-7 proxy: Web proxy products for layer-7 request forwarding are used, products such as anti-DDoS, CDN, and other cloud acceleration services.
- Layer-4 proxy: Web proxy products for layer-4 forwarding are used, products such as anti-DDoS.
- No proxy: No proxy products are deployed in front of WAF.

- If a proxy is deployed before WAF on your website, the WAF working mode cannot be switched to Bypassed. For more details, see Switching WAF Working Mode.
- If there is no proxy used for the protected website but you select Layer-7 proxy or Layer-4 proxy for Proxy Configured, WAF trusts the X-Forwarded-For field in the HTTP request header when obtaining the real source IP address. So there is no impact on your services.
- If you select Layer-7 proxy, WAF obtains the actual access IP address from the configured header field. For details, see Configuring a Traffic Identifier for a Known Attack Source.
- HTTP/2: If your website is accessible over HTTP and HTTPS, use HTTP/2.
HTTP/2 can be used only for access between the client and WAF on the condition that at least one origin server has HTTPS used for Client Protocol.

- To make Server Configuration works, there must be at least one server configuration record with Client Protocol set to HTTPS.
- HTTP/2 can work only when the client supports TLS 1.2 or earlier versions.
- Specify Policy. By default, system-generated policy is selected. You can select custom rules. For details, see Table 2.

If you are using WAF standard edition, only System-generated policy is available.
You can select a policy you configured. You can also customize rules after the domain name is connected to WAF.
Table 2 System-generated policies Edition
Policy
Description
Standard
Basic web protection (Log only mode and common checks)
The basic web protection defends against attacks such as SQL injections, XSS, remote overflow vulnerabilities, file inclusions, Bash vulnerabilities, remote command execution, directory traversal, sensitive file access, and command/code injections.
Professional and platinum
Basic web protection (Log only mode and common checks)
The basic web protection defends against attacks such as SQL injections, XSS, remote overflow vulnerabilities, file inclusions, Bash vulnerabilities, remote command execution, directory traversal, sensitive file access, and command/code injections.
Anti-crawler (Log only mode and Scanner feature)
WAF only logs web scanning tasks, such as vulnerability scanning and virus scanning, such as crawling behavior of OpenVAS and Nmap.

Log only: WAF only logs detected attacks instead of blocking them.
- IPv6 Protection: Enable IPv6 Protection if the domain name is accessible using an IPv6 address. After you enable it, WAF assigns an IPv6 address to the domain name.
- Click OK.
To enable WAF protection, there are three more steps, whitelisting WAF IP addresses, testing WAF, and routing your website traffic to WAF. You can click Later in this step. Then, finish those steps by referring to Step 4: Whitelist WAF Back-to-Source IP Addresses, Step 3: Test WAF, and Step 3: Modify the DNS Records of the Domain Name.Figure 4 Domain name added to WAF.

Verification
- By default, WAF detects the Access Status of each protected domain name on an hourly basis.
- Generally, if you have performed domain connection and Access Status is Accessible, the domain name is connected to WAF.
If a domain name has been connected to WAF but Access Status is Inaccessible, click
 to refresh. If Access Status is still Inaccessible, connect the domain name to WAF again by referring to Step 3: Modify the DNS Records of the Domain Name.
to refresh. If Access Status is still Inaccessible, connect the domain name to WAF again by referring to Step 3: Modify the DNS Records of the Domain Name.
Importing a New Certificate
If you set Client Protocol to HTTPS, an SSL certificate is required. You can perform the following steps to import a new certificate.
- Click Import New Certificate. In the displayed Import New Certificate dialog box, enter the certificate name and paste the certificate file and private key to the corresponding text boxes.
Figure 5 Import New Certificate
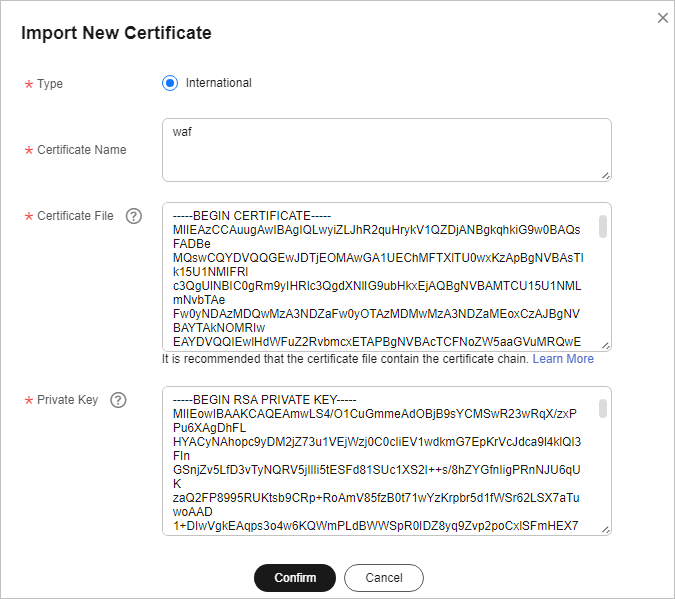

WAF encrypts and saves the private key to keep it safe.
Only .pem certificates can be used in WAF. If the certificate is not in .pem format, convert it into .pem locally by referring to Table 3 before uploading it.Table 3 Certificate conversion commands Format
Conversion Method
CER/CRT
Rename the cert.crt certificate file to cert.pem.
PFX
- Obtain a private key. For example, run the following command to convert cert.pfx into key.pem:
openssl pkcs12 -in cert.pfx -nocerts -out key.pem -nodes
- Obtain a certificate. For example, run the following command to convert cert.pfx into cert.pem:
openssl pkcs12 -in cert.pfx -nokeys -out cert.pem
P7B
- Convert a certificate. For example, run the following command to convert cert.p7b into cert.cer:
openssl pkcs7 -print_certs -in cert.p7b -out cert.cer
- Rename certificate file cert.cer to cert.pem.
DER
- Obtain a private key. For example, run the following command to convert privatekey.der into privatekey.pem:
openssl rsa -inform DER -outform PEM -in privatekey.der -out privatekey.pem
- Obtain a certificate. For example, run the following command to convert cert.cer into cert.pem:
openssl x509 -inform der -in cert.cer -out cert.pem

- Before running an OpenSSL command, ensure that the OpenSSL tool has been installed on the local host.
- If your local PC runs a Windows operating system, go to the command line interface (CLI) and then run the certificate conversion command.
- Obtain a private key. For example, run the following command to convert cert.pfx into key.pem:
- Click Confirm.
Example Configuration
There are some configuration examples provided for your reference in Configuration Example: Adding a Domain Name to WAF.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot